SECURITY AS A SERVICE
Cloud Computing represents one of the most significant shifts in information technology the industry has experienced. Reaching the point where computing functions as a utility has great potential, promising expansive innovations. One such innovation is the centralization of security resources.
The security industry has recognized the benefits of a standardized security framework for both the providers and consumers. In the context of a cloud service level agreement between providers and consumers, a standardized security framework takes the form of a document that specifies which security services are provided how and where.
With the maturation of security offerings based on standard frameworks, cloud consumers have recognized the need to centralize computing resources for providers and consumers.One of the milestones of the maturity of cloud as a platform for business operations is the adoption of Security as a Service (SecaaS) on a global scale and the recognition of how security can be enhanced.
The worldwide implementation of security as an outsourced commodity will eventually minimize the disparate variances and security voids.
SecaaS is looking at Enterprise security from the cloud – this is what differentiates it from most of the other work / research on cloud security.
Predominantly cloud security discussions have focused on how to migrate to the Cloud and how to ensure Confidentiality, Integrity, Availability and Location are maintained when using the Cloud.
SecaaS looks from the other side to secure systems and data in the cloud as well as hybrid and traditional enterprise networks via cloud-based services.
These systems may be in the cloud or more traditionally hosted within the customer’s premises. An example of this might be the hosted spam and AV filtering.
Overview. This domain will address the following topics:
I) The Ubiquity of Security as a Service in the Marketplace
II) Concerns when Implementing Security As a Service
III) Advantages of Implementing Security As a Service
IV) The Diversity of Services that can be categorized as Security As A
Service
Customers are both excited and nervous at the prospects of cloud computing. They are excited by the opportunities to reduce capital costs and excited for a chance to divest infrastructure management and focus on core competencies.
Most of all, they are excited by the agility offered by the on-demand provisioning of computing resources and the ability to align information technology with business strategies and needs more readily.
However, customers are also very concerned about the security risks of cloud computing and the loss of direct control over the security of systems for which they are accountable.
Vendors have attempted to satisfy this demand for security by offering security services in a cloud platform, but because these services take many forms and lack transparency regarding deployed security controls, they have caused market confusion and complicated the selection process.
This has led to limited adoption of cloud-based security services thus far. Security as a Service is experiencing an exponential growth with Gartner predicting that cloud-based security service usage will more than triple in many segments by 2013.
Numerous security vendors are now leveraging cloud-based models to deliver security solutions. This shift has occurred for a variety of reasons including greater economies of scale and streamlined delivery mechanisms.
Consumers are increasingly faced with evaluating security solutions that do not run on premises. Consumers need to understand the unique, diverse, and pervasive nature of cloud delivered security offerings so that they are in a position to evaluate the offerings and to understand if the offerings will meet their needs.
Despite the impressive array of benefits provided by cloud security services such as dynamic scalability, virtually unlimited resources, and greater economies of scale that exist with lower or no cost of ownership, there are concerns about security in the cloud environment. Some security concerns are around compliance, multi-tenancy, and vendor lock-in. While these are being cited as inhibitors to the migration of security into the cloud, these same concerns exist with traditional data centers.
Security in the cloud environment is often based on the concern that lack of visibility into security controls implemented means systems are not locked down as well as they are in traditional data centers and that the personnel lack the proper credentials and background checks. Security as a Service providers recognize the fragility of the relationship and often go to extreme lengths to ensure that their environment is locked down as much as possible. They often run background checks on their personnel that rival even the toughest government background checks, and they run them often. Physical and personnel security is one of the highest priorities of a Security as a Service provider.
Compliance has been raised as a concern given the global regulatory environment. Security as a Service providers have also recognized this and have gone to great efforts to demonstrate their ability to not only meet but exceed these requirements or to ensure that it is integrated into a client’s network. Security as a Service providers should be cognizant of the geographical and regional regulations that affect the services and their consumers, and this can be built into the offerings and service implementations. The most prudent Security as a Service providers often enlist mediation and legal services to preemptively resolve the regulatory needs of the consumer with the regional regulatory requirements of a jurisdiction. When deploying Security as a Service in a highly regulated industry or environment, agreement on the metrics defining the service level required to achieve regulatory objectives should be negotiated in parallel with the SLA documents defining service.
As with any cloud service, multi-tenancy presents concerns of data leakage between virtual instances. While customers are concerned about this, the Security as a Service providers are also highly concerned in light of the litigious nature of modern business. As a result, a mature offering may take significant precautions to ensure data is highly compartmentalized and any data that is shared is anonymized to protect the identity and source. This applies equally to the data being monitored by the SecaaS provider and to the data held by them such as log and audit data from the client’s systems (both cloud and non-cloud) that they monitor.
Another approach to the litigious nature of multi-tenant environments is increased analytics coupled with semantic processing. Resource descriptors and applied jurimetrics, a process through which legal reasoning is interpreted as high-level concepts and expressed in a machine-readable format, may be employed proactively to resolve any legal ambiguity regarding a shared resource.
When utilizing a Security as a Service vendor, an enterprise places some, many or all security logging, compliance, and reporting into the custody of a provider that might sometimes have proprietary standards. In the event the enterprise seeks a new provider, they must concern themselves with an orderly transition and somehow find a way for the existing data and log files to be translated correctly and in a forensically sound manner.
It is important to note that other than multi-tenancy, each of these concerns is not “cloud unique” but are problems faced by both in-house models and outsourcing models. For this reason, non-proprietary unified security controls, such as those proposed by the Cloud Security Alliance Cloud Control Matrix, are needed to help enterprises and vendors benefit from the Security as a Service environment.
The potential strategic benefits of leveraging centralized security services are well understood by technical experts who witness the daily efficiencies gained. Just as cloud computing offers many advantages to both providers and consumers, Cloud Security as a Service offers many significant benefits due to a number of factors, including aggregation of knowledge, broad actionable intelligence, and having a full complement of security professionals on hand at all times, to name a few. Companies that are actively involved in the centralization and standardization of security best practices typically gain significant medium and long-term cost savings and competitive benefits over their rivals in the market due to the efficiencies gained. Security delivered as a service enables the users of security services to measure each vendor by a singular security standard thus better understanding what they are getting.
Companies that employ third party security service providers gain a competitive edge over their peers due to early access to information helpful in understanding the risk proposition of a given IT strategy. Furthermore, through the use of a centralized security infrastructure, consumers are better able to stem the inclusion of undesirable content. Companies making use of a third party to report on regulatory compliance and measure obligatory predicates —the inherited legal and contractual obligations connected to identities and data—might result in the avoidance of costly litigation and fines that their competitors are vulnerable to. Once holistic security services are adopted and implemented, providers reap the competitive benefits of being able to assure their clients that they meet security best practice. Clients making use of these services have the advantage of being able to point to security providers as a part of their compliance framework and to third party assurance providers for proof of the achievement of service level agreement obligations.
There are many clear-cut benefits of security as a service. Transparency provided by a third party assurance service enables customers to understand exactly what they are getting, enabling easier comparison of vendor services and holding vendors to clear and agreed standards. Migration services enable the migration of data and services from one vendor to another. By leveraging migration services, consumers and providers are better enabled to exert market
pressures on their tertiary suppliers, enhancing the value for the enterprises that consume the services and securing the supply chain.
Security as a Service is more than an outsourcing model for security management; it is an essential component in secure business resiliency and continuity. As a business resiliency control, Security as a Service offers a number of benefits. Due to the elastic model of services delivered via the cloud, customers need only pay for the amount they require, such as the number of workstations to be protected and not for the supporting infrastructure and staffing to support the various security services. A security focused provider offers greater security expertise than is typically available within an organization. Finally, outsourcing administrative tasks, such as log management, can save time and money, allowing an organization to devote more resources to its core competencies.
Gartner predicts that cloud-based security controls for messaging applications such as anti-malware and anti-spam programs will generate 60 percent of the revenue in that industry sector by 2013.
The areas of Cloud Security as a Service that most likely will interest consumers and security professionals are:
a) Identity Services and Access Management Services
b) Data Loss Prevention (DLP)
c) Web Security
d) Email Security
e) Security Assessments
f) Intrusion Management, Detection, and Prevention (IDS/IPS)
g) Security Information and Event Management (SIEM)
h) Encryption
i) Business Continuity and Disaster Recovery
j) Network Security
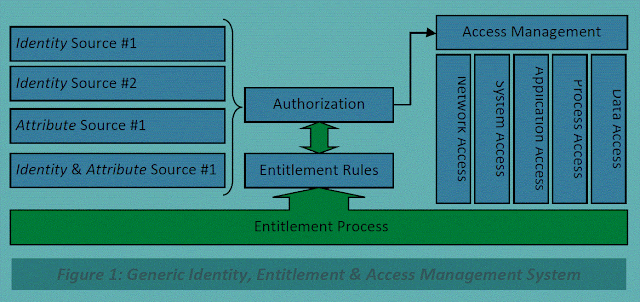
Identity-as-a-service is a generic term that covers one or many of the services that may comprise an identity eco-system, such as Policy Enforcement Points (PEP-as-a-service), Policy Decision Points (PDP-as-a-service), Policy Access Points (PAP-as-a-service), services that provide Entities with Identity, services that provide attributes, and services that provide reputation.
All these Identity services can be provided as a single stand-alone service, as a mix-and-match service from multiple providers, or today most probably a hybrid solution of public and private, traditional IAM, and cloud services.
These Identity services should provide controls for identities, access, and privileges management. Identity services need to include people, processes, and systems that are used to manage access to enterprise resources by assuring the identity of an entity is verified, then granting the correct level of access based on this assured identity. Audit logs of activities such as successful and failed authentication and access attempts should be managed by the application / solution or the SIEM service. Identity, Entitlement, and Access Management services are a Protective and Preventative technical control.
Monitoring, protecting, and demonstrating protection of data at rest, in motion, and in use both in the cloud and on premises, Data Loss Prevention (DLP) services offer protection of data usually by running as a client on desktops / servers and enforcing policies around what actions are authorized for particular data content. Where these differ from broad rules like ‘no ftp’ or ‘no uploads to web sites’ is the level to which they understand data, e.g., the user can specify no documents with numbers that look like credit cards can be emailed; anything saved to USB storage is automatically encrypted and can only be unencrypted on another office owned machine with a correctly installed DLP client; and only clients with functioning DLP software can open files from the file server. Within the cloud, DLP services may be offered as something that is provided as part of the build such that all servers built for that client get the DLP software installed with an agreed set of rules deployed. In addition, DLP may leverage central ID- or cloud brokers to enforce usage profiles. The ability to leverage a service to monitor and control data flows from an enterprise to the various tiers in the cloud service supply chain may be used as a preventative control for transborder transport, and subsequent loss, of regulated data such as PII. This DLP offering is a preventative technical control.
PII-Personally Identifiable Information
Web Security is real-time protection offered either on premise through software / appliance installation or via the Cloud by proxying or redirecting web traffic to the cloud provider. This provides an added layer of protection on top of other protection such as anti-malware software to prevent malware from entering the enterprise via activities such as web browsing. Policy rules around types of web access and the time frames when this is allowed can also be enforced via these technologies. Application authorization management can be used to provide an extra level of granular and contextual security enforcement for web applications. Web Security is a protective, detective, and reactive technical control.
Email Security should provide control over inbound and outbound email, protecting the organization from phishing, malicious attachments, enforcing corporate polices such as acceptable use and spam prevention, and providing business continuity options. In addition, the solution should allow for policy-based encryption of emails as well as integrating with various email server solutions. Digital signatures enabling identification and non-repudiation are also features of many email security solutions. The Email Security offering is a protective, detective, and reactive technical control.
Security assessments are third party or customer-driven audits of cloud services or assessments of on premises systems via cloud provided solutions based on industry standards. Traditional security assessments for infrastructure, applications and compliance audits are well defined and supported by multiple standards such as NIST, ISO, and CIS 144. A relatively mature toolset exists, and a number of tools have been implemented using the SecaaS delivery model. In the SecaaS delivery model, subscribers get the typical benefits of this cloud-computing variant—elasticity, negligible setup time, low administration overhead, and pay per use with low initial investments.
While not the focus of this effort, additional challenges arise when these tools are used to audit cloud environments. Multiple organizations, including the CSA have been working on the guidelines to help organizations understand the additional challenges:
a) Virtualization awareness of the tool, frequently necessary for IaaS platform auditing
b) Support for common web frameworks in PaaS applications
c) Compliance Controls for Iaas, PaaS, and Saas platforms
d) Automated incident and breach notification tools for maintenance of cloud supply chain integrity
e) Standardized questionnaires for XaaS environments, that help address:
- What should be tested in a cloud environment?
- How does one assure data isolation in a multi-tenant environment?
- What should appear in a typical infrastructure vulnerability report?
- Is it acceptable to use results provided by cloud provider?
Intrusion Detection/Prevention systems monitor behavior patterns using rule-based, heuristic, or behavioral models to detect anomalies in activity that present risks to the enterprise. Network IDS/IPS have become widely used over the past decade because of the capability to provide a granular view of what is happening within an enterprise network. The IDS/IPS monitors network traffic and compares the activity to a baseline via rule-based engine or statistical analysis. IDS is typically deployed in a passive mode to passively monitor sensitive segments of a client’s network whereas the IPS is configured to play an active role in the defense of the clients network. In a traditional infrastructure, this could include De-Militarized Zones (DMZ’s)145 segmented by firewalls or routers where corporate Web servers are locate or monitoring connections to an internal database. Within the cloud, IDS systems often focus on virtual infrastructure and cross-hypervisor activity where coordinated attacks can disrupt multiple tenants and create system chaos. Intrusion Detection Systems are detective technical controls, and Intrusion Prevention Systems are detective, protective, and reactive technical controls.
144 CIS-Center for Internet Security
145 DMZ-De-Militarized Zone
Security Information and Event Management (SIEM) systems aggregate (via push or pull mechanisms) log and event data from virtual and real networks, applications, and systems. This information is then correlated and analyzed to provide real time reporting and alerting on information or events that may require intervention or other types of responses. The logs are typically collected and archived in a manner that prevents tampering to enable their use as evidence in any investigations or historical reporting. The SIEM Security as a Service offering is a Detective technical control but can be configured to be a protective and reactive technical control.
Encryption is the process of obfuscating/ encoding data using cryptographic algorithms, the product of which is encrypted data (referred to as cipher-text). Only the intended recipient or system that is in possession of the correct key can decode (un-encrypt) the cipher-text. Encryption for obfuscation systems typically consist of one or more algorithms that are computationally difficult (or infeasible) to break one or more keys, and the systems, processes, and procedures to manage encryption, decryption, and keys. Each part is effectively useless without the other, e.g., the best algorithm is easy to “crack” if an attacker can access the keys due to weak processes.
In the case of one-way cryptographic functions, a digest or hash is created instead. One-way cryptographic functions include hashing, digital signatures, certificate generation and renewal, and key exchanges. These systems typically consist of one or more algorithms that are easily replicated but very resistant to forgery, along with the processes and procedures to manage them. Encryption when outsourced to a Security as a Service provider is classified as a protective and detective technical control.
Business Continuity and Disaster Recovery are the measures designed and implemented to ensure operational resiliency in the event of any service interruptions. They provide flexible and reliable failover and DR solutions for required services in the event of a service interruption, whether natural or man-made. For example, in the event of a disaster scenario at one location, machines at different locations may protect applications in that location. This Security as a Service offering is a reactive, protective, and detective technical control.
Network Security consists of security services that restrict or allocate access and that distribute, monitor, log, and protect the underlying resource services.
Architecturally, network security provides services that address security controls at the network in aggregate or those controls specifically addressed at the individual network of each underlying resource. In cloud / virtual environments and hybrid environments, network security is likely to be provided by virtual devices alongside traditional physical devices. Tight integration with the hypervisor to ensure full visibility of all traffic on the virtual network layer is key. These Network Security offerings include detective, protective, and reactive technical controls.
A) Implementers may employ pattern recognition of user activities..
B) Implementers may employ secure legal mediation of security metrics for SLA expectation management
C) Implementers may employ provide trusted channels for penetration testing.
a) Implementers should ensure secure communication channels between tenant and consumer.
b) Providers should supply automated secure and continuous notification throughout the supply chain on a need-to-know basis.
c) Providers should supply secured logging of internal operations for service level agreement compliance.
d) Consumers should request addition of third party audit and SLA mediation services.
e) All parties should enable Continuous Monitoring of all interfaces through standardized security interfaces such as SCAP (NIST), CYBEX (ITU-T), or RID & IODEF (IETF).
1) Providers of IaaS must provide cloud customers provisioning/de-provisioning of accounts (of both cloud & on-premise applications and resources).
2) Providers of IaaS must provide cloud customers authentication (multiple forms and factors).
3) Providers of IaaS must provide cloud customers identity life cycle management.
4) Providers of IaaS must provide cloud customers directory services.
5) Providers of IaaS must provide cloud customers directory synchronization (multi-lateral as required).
6) Providers of IaaS must provide cloud customers federated SSO.
7) Providers of IaaS must provide cloud customers web SSO (granular access enforcement & session management - different from federated SSO).
8) Providers of IaaS must provide privileged session monitoring.
9) Providers of IaaS must provide granular access management.
10) Providers of IaaS must provide tamper-proof storage of audit records (including an option for non-repudiation).
11) Providers of IaaS must provide policy management (incl. authorization management, role management, compliance policy management).
12) Providers of IaaS must provide cloud customers authorization (both user and application/system).
13) Providers of IaaS must provide cloud customers authorization token management and provisioning.
14) Providers of IaaS must provide cloud customers user profile and entitlement management (both user and application/system).
15) Providers of IaaS must provide cloud customers support for policy and regulatory compliance monitoring and/or reporting.
16) Providers of IaaS must provide cloud customers federated provisioning of cloud applications.
17) Providers of IaaS must provide privileged user and password management (including administrative, shared, system and application accounts).
18) Providers of IaaS must provide cloud customers Role-Based Access Control (RBAC) (where supported by the underlying system/service).
19) Providers of IaaS must provide cloud customers optionally support DLP integration.
20) Providers of IaaS must provide cloud customers optionally support granular activity auditing broken down by individual.
21) Providers of IaaS must provide cloud customers segregation of duties based on identity entitlement.
22) Providers of IaaS must provide cloud customers compliance-centric reporting.
23) Providers of IaaS must provide cloud customers centralized policy management.
25) Providers of IaaS must provide cloud customers usable management interfaces.
26) Providers of IaaS must provide cloud customers unified access control & audit.
27) Providers of IaaS must provide cloud customers Interoperability and heterogeneity among various providers.
28) Providers of IaaS must provide cloud customers scalability.
1) Providers of DLP must provide cloud customers with data labeling and classification.
2) Providers of DLP must provide cloud customers with identification of Sensitive Data.
3) Providers of DLP must provide cloud customers with predefined policies for major regulatory statues.
4) Providers of DLP must provide cloud customers with context detection heuristics.
5) Providers of DLP must provide cloud customers with structured data matching (data-at-rest).
6) Providers of DLP must provide cloud customers with SQL regular expression detection.
7) Providers of DLP must provide cloud customers with traffic spanning (data-in-motion) detection.
8) Providers of DLP must provide cloud customers with Real Time User Awareness.
9) Providers of DLP must provide cloud customers with security level assignment.
10) Providers of DLP must provide cloud customers with custom attribute lookup.
11) Providers of DLP must provide cloud customers with automated incident response.
12) Providers of DLP must provide cloud customers with signing of data.
13) Providers of DLP must provide cloud customers with cryptographic data protection and access control.
14) Providers of DLP must provide cloud customers with machine-readable policy language.
1) Providers of Web Services SecaaS must provide cloud customers with web monitoring and filtering.
2) Providers of Web Services SecaaS must provide cloud customers with Malware, Spyware, and Bot Network analyzer and blocking.
3) Providers of Web Services SecaaS must provide cloud customers with phishing site blocker.
4) Providers of Web Services SecaaS must provide cloud customers with instant messaging scanning.
5) Providers of Web Services SecaaS must provide cloud customers with email security.
6) Providers of Web Services SecaaS must provide cloud customers with bandwidth management / traffic control.
7) Providers of Web Services SecaaS must provide cloud customers with Data Loss Prevention.
8) Providers of Web Services SecaaS must provide cloud customers with fraud prevention.
9) Providers of Web Services SecaaS must provide cloud customers with Web Access Control.
10) Providers of Web Services SecaaS must provide cloud customers with backup.
11) Providers of Web Services SecaaS must provide cloud customers with SSL (decryption / hand off).
12) Providers of Web Services SecaaS must provide cloud customers with usage policy enforcement.
13) Providers of Web Services SecaaS must provide cloud customers with vulnerability management.
14) Providers of Web Services SecaaS must provide must provide cloud customers with web intelligence reporting.
1) Providers of Email Security SecaaS must provide cloud customers with accurate filtering to block spam and phishing.
2) Providers of Email Security SecaaS must provide cloud customers with deep protection against viruses and spyware before they enter the enterprise perimeter.
3) Providers of Email Security SecaaS must provide cloud customers with flexible policies to define granular mail flow and encryption.
4) Providers of Email Security SecaaS must provide cloud customers with rich, interactive reports and correlate real-time reporting.
5) Providers of Email Security SecaaS must provide cloud customers with deep content scanning to enforce policies.
6) Providers of Email Security SecaaS must provide cloud customers with the option to encrypt some / all emails based on policy.
7) Providers of Email Security SecaaS must provide cloud customers with integration capability to various email server solutions.
1) Providers of Security Assessment SecaaS must provide cloud customers with detailed governance processes and metrics (Implementers should define and document and process by which policies are set and decision making is executed).
2) Providers of Security Assessments and Governance offerings should implement an automated solution for notifying members of their immediate supply chain in the event of breach or security incident.
3) Providers of Security Assessment SecaaS must provide cloud customers with proper risk management (Implementers should define and document and process for ensuring that important business processes and behaviors remain within the tolerances associated with those policies and decisions).
4) Providers of Security Assessment SecaaS must provide cloud customers with details of compliance (Implementers should define and document process-of-adherence to policies and decisions).
5) Providers of Security Assessment SecaaS must provide cloud customers with policies that can be derived from internal directives, procedures, and requirements or external laws, regulations, standards and agreements.
6) Providers of Security Assessment SecaaS must provide cloud customers with technical compliance audits (automated auditing of configuration settings in devices, operating systems, databases, and applications).
7) Providers of Security Assessment SecaaS must provide cloud customers with application security assessments (automated auditing of custom applications).
8) Providers of an assessment and governance service offering must provide cloud customers with vulnerability assessments—automated probing of network devices, computers, and applications for known vulnerabilities and configuration issues.
9) Providers of Security Assessment SecaaS must provide cloud customers with penetration testing (exploitation of vulnerabilities and configuration issues to gain access to an environment, network or computer, typically requiring manual assistance)
10) Providers of Security Assessment SecaaS must provide cloud customers with a security rating.
1) Providers of Intrusion Detection SecaaS must provide cloud customers with identification of intrusions and policy violations.
2) Providers of Intrusion Detection SecaaS must provide cloud customers with automatic or manual remediation actions.
3) Providers of Intrusion Detection SecaaS must provide cloud customers with Coverage for Workloads, Virtualization Layer (VMM/Hypervisor) Management Plane
4) Providers of Intrusion Detection SecaaS must provide cloud customers with deep packet inspection using one or more of the following techniques: statistical, behavioral, signature, heuristic.
5) Providers of Intrusion Detection SecaaS must provide cloud customers with system call monitoring.
6) Providers of Intrusion Detection SecaaS must provide cloud customers with system/application log inspection.
7) Providers of Intrusion Detection SecaaS must provide cloud customers with integrity monitoring OS (files, registry, ports, processes, installed software, etc.)
8) Providers of Intrusion Detection SecaaS must provide cloud customers with integrity monitoring VMM/Hypervisor.
9) Providers of Intrusion Detection SecaaS must provide cloud customers with VM Image Repository Monitoring.
1) Providers of SIEM SecaaS must provide cloud customers with real time log /event collection, de-duplication, normalization, aggregation and visualization.
2) Providers of SIEM SecaaS must provide cloud customers with forensics support.
3) Providers of SIEM SecaaS must provide cloud customers with reporting and support.
4) Providers of SIEM SecaaS must provide cloud customers with IR support.
5) Providers of SIEM SecaaS must provide cloud customers with anomaly detection not limited to email.
6) Providers of SIEM SecaaS must provide cloud customers with detailed reporting.
7) Providers of SIEM SecaaS must provide cloud customers with flexible data retention periods and flexible policy management
1) Providers of Encryption SecaaS must provide cloud customers with protection of data in transit.
2) Providers of Encryption SecaaS must provide cloud customers with protection of data at rest.
3) Providers of Encryption SecaaS must provide cloud customers with key and policy management.
4) Providers of Encryption SecaaS must provide cloud customers with protection of cached data.
1) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with flexible infrastructure.
2) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with secure backup.
3) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with monitored operations.
4) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with third party service connectivity.
5) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with replicated infrastructure component.
6) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with replicated data (core / critical systems).
7) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with data and/or application recovery.
8) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with alternate sites of operation.
9) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with tested and measured processes and operations to ensure operational resiliency.
10) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with geographically distributed data centers / infrastructure.
11) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with Network survivability.
1) Providers of Network Security SecaaS must provide cloud customers with details of data threats.
2) Providers of Network Security SecaaS must provide cloud customers with details of access control threats.
3) Providers of Network Security SecaaS must provide cloud customers with access and authentication controls.
4) Providers of Network Security SecaaS must provide cloud customers with security gateways (firewalls, WAF, SOA/API).
5) Providers of Network Security SecaaS must provide cloud customers with security products (IDS/IPS, Server Tier Firewall, File Integrity Monitoring, DLP, Anti-Virus, Anti-Spam).
6) Providers of Network Security SecaaS must provide cloud customers with security monitoring and incident response.
7) Providers of Network Security SecaaS must provide cloud customers with DoS protection/mitigation.
8) Providers of Network Security SecaaS must provide cloud customers with Secure “base services” like DNSSEC, NTP, OAuth, SNMP, management network segmentation, and security.
9) Providers of Network Security SecaaS must provide cloud customers with traffic / netflow monitoring.
10) Providers of Network Security SecaaS must provide cloud customers integration with Hypervisor layer.
===// END //===
The security industry has recognized the benefits of a standardized security framework for both the providers and consumers. In the context of a cloud service level agreement between providers and consumers, a standardized security framework takes the form of a document that specifies which security services are provided how and where.
With the maturation of security offerings based on standard frameworks, cloud consumers have recognized the need to centralize computing resources for providers and consumers.One of the milestones of the maturity of cloud as a platform for business operations is the adoption of Security as a Service (SecaaS) on a global scale and the recognition of how security can be enhanced.
The worldwide implementation of security as an outsourced commodity will eventually minimize the disparate variances and security voids.
SecaaS is looking at Enterprise security from the cloud – this is what differentiates it from most of the other work / research on cloud security.
Predominantly cloud security discussions have focused on how to migrate to the Cloud and how to ensure Confidentiality, Integrity, Availability and Location are maintained when using the Cloud.
SecaaS looks from the other side to secure systems and data in the cloud as well as hybrid and traditional enterprise networks via cloud-based services.
These systems may be in the cloud or more traditionally hosted within the customer’s premises. An example of this might be the hosted spam and AV filtering.
Overview. This domain will address the following topics:
I) The Ubiquity of Security as a Service in the Marketplace
II) Concerns when Implementing Security As a Service
III) Advantages of Implementing Security As a Service
IV) The Diversity of Services that can be categorized as Security As A
Service
14.1 Ubiquity of Security as a Service
Customers are both excited and nervous at the prospects of cloud computing. They are excited by the opportunities to reduce capital costs and excited for a chance to divest infrastructure management and focus on core competencies.
Most of all, they are excited by the agility offered by the on-demand provisioning of computing resources and the ability to align information technology with business strategies and needs more readily.
However, customers are also very concerned about the security risks of cloud computing and the loss of direct control over the security of systems for which they are accountable.
Vendors have attempted to satisfy this demand for security by offering security services in a cloud platform, but because these services take many forms and lack transparency regarding deployed security controls, they have caused market confusion and complicated the selection process.
This has led to limited adoption of cloud-based security services thus far. Security as a Service is experiencing an exponential growth with Gartner predicting that cloud-based security service usage will more than triple in many segments by 2013.
Numerous security vendors are now leveraging cloud-based models to deliver security solutions. This shift has occurred for a variety of reasons including greater economies of scale and streamlined delivery mechanisms.
Consumers are increasingly faced with evaluating security solutions that do not run on premises. Consumers need to understand the unique, diverse, and pervasive nature of cloud delivered security offerings so that they are in a position to evaluate the offerings and to understand if the offerings will meet their needs.
14.2 Concerns When Implementing Security as a Service
Despite the impressive array of benefits provided by cloud security services such as dynamic scalability, virtually unlimited resources, and greater economies of scale that exist with lower or no cost of ownership, there are concerns about security in the cloud environment. Some security concerns are around compliance, multi-tenancy, and vendor lock-in. While these are being cited as inhibitors to the migration of security into the cloud, these same concerns exist with traditional data centers.
Security in the cloud environment is often based on the concern that lack of visibility into security controls implemented means systems are not locked down as well as they are in traditional data centers and that the personnel lack the proper credentials and background checks. Security as a Service providers recognize the fragility of the relationship and often go to extreme lengths to ensure that their environment is locked down as much as possible. They often run background checks on their personnel that rival even the toughest government background checks, and they run them often. Physical and personnel security is one of the highest priorities of a Security as a Service provider.
Compliance has been raised as a concern given the global regulatory environment. Security as a Service providers have also recognized this and have gone to great efforts to demonstrate their ability to not only meet but exceed these requirements or to ensure that it is integrated into a client’s network. Security as a Service providers should be cognizant of the geographical and regional regulations that affect the services and their consumers, and this can be built into the offerings and service implementations. The most prudent Security as a Service providers often enlist mediation and legal services to preemptively resolve the regulatory needs of the consumer with the regional regulatory requirements of a jurisdiction. When deploying Security as a Service in a highly regulated industry or environment, agreement on the metrics defining the service level required to achieve regulatory objectives should be negotiated in parallel with the SLA documents defining service.
As with any cloud service, multi-tenancy presents concerns of data leakage between virtual instances. While customers are concerned about this, the Security as a Service providers are also highly concerned in light of the litigious nature of modern business. As a result, a mature offering may take significant precautions to ensure data is highly compartmentalized and any data that is shared is anonymized to protect the identity and source. This applies equally to the data being monitored by the SecaaS provider and to the data held by them such as log and audit data from the client’s systems (both cloud and non-cloud) that they monitor.
Another approach to the litigious nature of multi-tenant environments is increased analytics coupled with semantic processing. Resource descriptors and applied jurimetrics, a process through which legal reasoning is interpreted as high-level concepts and expressed in a machine-readable format, may be employed proactively to resolve any legal ambiguity regarding a shared resource.
When utilizing a Security as a Service vendor, an enterprise places some, many or all security logging, compliance, and reporting into the custody of a provider that might sometimes have proprietary standards. In the event the enterprise seeks a new provider, they must concern themselves with an orderly transition and somehow find a way for the existing data and log files to be translated correctly and in a forensically sound manner.
It is important to note that other than multi-tenancy, each of these concerns is not “cloud unique” but are problems faced by both in-house models and outsourcing models. For this reason, non-proprietary unified security controls, such as those proposed by the Cloud Security Alliance Cloud Control Matrix, are needed to help enterprises and vendors benefit from the Security as a Service environment.
14.3 Advantages When Implementing Security as a Service
The potential strategic benefits of leveraging centralized security services are well understood by technical experts who witness the daily efficiencies gained. Just as cloud computing offers many advantages to both providers and consumers, Cloud Security as a Service offers many significant benefits due to a number of factors, including aggregation of knowledge, broad actionable intelligence, and having a full complement of security professionals on hand at all times, to name a few. Companies that are actively involved in the centralization and standardization of security best practices typically gain significant medium and long-term cost savings and competitive benefits over their rivals in the market due to the efficiencies gained. Security delivered as a service enables the users of security services to measure each vendor by a singular security standard thus better understanding what they are getting.
14.3.1 Competitive Advantages
Companies that employ third party security service providers gain a competitive edge over their peers due to early access to information helpful in understanding the risk proposition of a given IT strategy. Furthermore, through the use of a centralized security infrastructure, consumers are better able to stem the inclusion of undesirable content. Companies making use of a third party to report on regulatory compliance and measure obligatory predicates —the inherited legal and contractual obligations connected to identities and data—might result in the avoidance of costly litigation and fines that their competitors are vulnerable to. Once holistic security services are adopted and implemented, providers reap the competitive benefits of being able to assure their clients that they meet security best practice. Clients making use of these services have the advantage of being able to point to security providers as a part of their compliance framework and to third party assurance providers for proof of the achievement of service level agreement obligations.
14.3.2 Improved Vendor Client Relationship
There are many clear-cut benefits of security as a service. Transparency provided by a third party assurance service enables customers to understand exactly what they are getting, enabling easier comparison of vendor services and holding vendors to clear and agreed standards. Migration services enable the migration of data and services from one vendor to another. By leveraging migration services, consumers and providers are better enabled to exert market
pressures on their tertiary suppliers, enhancing the value for the enterprises that consume the services and securing the supply chain.
14.4 Diversity of Existing Security as a Service Offerings
Security as a Service is more than an outsourcing model for security management; it is an essential component in secure business resiliency and continuity. As a business resiliency control, Security as a Service offers a number of benefits. Due to the elastic model of services delivered via the cloud, customers need only pay for the amount they require, such as the number of workstations to be protected and not for the supporting infrastructure and staffing to support the various security services. A security focused provider offers greater security expertise than is typically available within an organization. Finally, outsourcing administrative tasks, such as log management, can save time and money, allowing an organization to devote more resources to its core competencies.
Gartner predicts that cloud-based security controls for messaging applications such as anti-malware and anti-spam programs will generate 60 percent of the revenue in that industry sector by 2013.
The areas of Cloud Security as a Service that most likely will interest consumers and security professionals are:
a) Identity Services and Access Management Services
b) Data Loss Prevention (DLP)
c) Web Security
d) Email Security
e) Security Assessments
f) Intrusion Management, Detection, and Prevention (IDS/IPS)
g) Security Information and Event Management (SIEM)
h) Encryption
i) Business Continuity and Disaster Recovery
j) Network Security
14.4.1 Identity, Entitlement, and Access Management Services
Identity-as-a-service is a generic term that covers one or many of the services that may comprise an identity eco-system, such as Policy Enforcement Points (PEP-as-a-service), Policy Decision Points (PDP-as-a-service), Policy Access Points (PAP-as-a-service), services that provide Entities with Identity, services that provide attributes, and services that provide reputation.
All these Identity services can be provided as a single stand-alone service, as a mix-and-match service from multiple providers, or today most probably a hybrid solution of public and private, traditional IAM, and cloud services.
These Identity services should provide controls for identities, access, and privileges management. Identity services need to include people, processes, and systems that are used to manage access to enterprise resources by assuring the identity of an entity is verified, then granting the correct level of access based on this assured identity. Audit logs of activities such as successful and failed authentication and access attempts should be managed by the application / solution or the SIEM service. Identity, Entitlement, and Access Management services are a Protective and Preventative technical control.
14.4.2 Data Loss Prevention
Monitoring, protecting, and demonstrating protection of data at rest, in motion, and in use both in the cloud and on premises, Data Loss Prevention (DLP) services offer protection of data usually by running as a client on desktops / servers and enforcing policies around what actions are authorized for particular data content. Where these differ from broad rules like ‘no ftp’ or ‘no uploads to web sites’ is the level to which they understand data, e.g., the user can specify no documents with numbers that look like credit cards can be emailed; anything saved to USB storage is automatically encrypted and can only be unencrypted on another office owned machine with a correctly installed DLP client; and only clients with functioning DLP software can open files from the file server. Within the cloud, DLP services may be offered as something that is provided as part of the build such that all servers built for that client get the DLP software installed with an agreed set of rules deployed. In addition, DLP may leverage central ID- or cloud brokers to enforce usage profiles. The ability to leverage a service to monitor and control data flows from an enterprise to the various tiers in the cloud service supply chain may be used as a preventative control for transborder transport, and subsequent loss, of regulated data such as PII. This DLP offering is a preventative technical control.
PII-Personally Identifiable Information
14.4.3 Web Security
Web Security is real-time protection offered either on premise through software / appliance installation or via the Cloud by proxying or redirecting web traffic to the cloud provider. This provides an added layer of protection on top of other protection such as anti-malware software to prevent malware from entering the enterprise via activities such as web browsing. Policy rules around types of web access and the time frames when this is allowed can also be enforced via these technologies. Application authorization management can be used to provide an extra level of granular and contextual security enforcement for web applications. Web Security is a protective, detective, and reactive technical control.
14.4.4 Email Security
Email Security should provide control over inbound and outbound email, protecting the organization from phishing, malicious attachments, enforcing corporate polices such as acceptable use and spam prevention, and providing business continuity options. In addition, the solution should allow for policy-based encryption of emails as well as integrating with various email server solutions. Digital signatures enabling identification and non-repudiation are also features of many email security solutions. The Email Security offering is a protective, detective, and reactive technical control.
14.4.5 Security Assessment
Security assessments are third party or customer-driven audits of cloud services or assessments of on premises systems via cloud provided solutions based on industry standards. Traditional security assessments for infrastructure, applications and compliance audits are well defined and supported by multiple standards such as NIST, ISO, and CIS 144. A relatively mature toolset exists, and a number of tools have been implemented using the SecaaS delivery model. In the SecaaS delivery model, subscribers get the typical benefits of this cloud-computing variant—elasticity, negligible setup time, low administration overhead, and pay per use with low initial investments.
While not the focus of this effort, additional challenges arise when these tools are used to audit cloud environments. Multiple organizations, including the CSA have been working on the guidelines to help organizations understand the additional challenges:
a) Virtualization awareness of the tool, frequently necessary for IaaS platform auditing
b) Support for common web frameworks in PaaS applications
c) Compliance Controls for Iaas, PaaS, and Saas platforms
d) Automated incident and breach notification tools for maintenance of cloud supply chain integrity
e) Standardized questionnaires for XaaS environments, that help address:
- What should be tested in a cloud environment?
- How does one assure data isolation in a multi-tenant environment?
- What should appear in a typical infrastructure vulnerability report?
- Is it acceptable to use results provided by cloud provider?
14.4.6 Intrusion Detection/Prevention (IDS/IPS)
Intrusion Detection/Prevention systems monitor behavior patterns using rule-based, heuristic, or behavioral models to detect anomalies in activity that present risks to the enterprise. Network IDS/IPS have become widely used over the past decade because of the capability to provide a granular view of what is happening within an enterprise network. The IDS/IPS monitors network traffic and compares the activity to a baseline via rule-based engine or statistical analysis. IDS is typically deployed in a passive mode to passively monitor sensitive segments of a client’s network whereas the IPS is configured to play an active role in the defense of the clients network. In a traditional infrastructure, this could include De-Militarized Zones (DMZ’s)145 segmented by firewalls or routers where corporate Web servers are locate or monitoring connections to an internal database. Within the cloud, IDS systems often focus on virtual infrastructure and cross-hypervisor activity where coordinated attacks can disrupt multiple tenants and create system chaos. Intrusion Detection Systems are detective technical controls, and Intrusion Prevention Systems are detective, protective, and reactive technical controls.
144 CIS-Center for Internet Security
145 DMZ-De-Militarized Zone
14.4.7 Security Information & Event Management (SIEM)
Security Information and Event Management (SIEM) systems aggregate (via push or pull mechanisms) log and event data from virtual and real networks, applications, and systems. This information is then correlated and analyzed to provide real time reporting and alerting on information or events that may require intervention or other types of responses. The logs are typically collected and archived in a manner that prevents tampering to enable their use as evidence in any investigations or historical reporting. The SIEM Security as a Service offering is a Detective technical control but can be configured to be a protective and reactive technical control.
14.4.8 Encryption
Encryption is the process of obfuscating/ encoding data using cryptographic algorithms, the product of which is encrypted data (referred to as cipher-text). Only the intended recipient or system that is in possession of the correct key can decode (un-encrypt) the cipher-text. Encryption for obfuscation systems typically consist of one or more algorithms that are computationally difficult (or infeasible) to break one or more keys, and the systems, processes, and procedures to manage encryption, decryption, and keys. Each part is effectively useless without the other, e.g., the best algorithm is easy to “crack” if an attacker can access the keys due to weak processes.
In the case of one-way cryptographic functions, a digest or hash is created instead. One-way cryptographic functions include hashing, digital signatures, certificate generation and renewal, and key exchanges. These systems typically consist of one or more algorithms that are easily replicated but very resistant to forgery, along with the processes and procedures to manage them. Encryption when outsourced to a Security as a Service provider is classified as a protective and detective technical control.
14.4.9 Business Continuity and Disaster Recovery
Business Continuity and Disaster Recovery are the measures designed and implemented to ensure operational resiliency in the event of any service interruptions. They provide flexible and reliable failover and DR solutions for required services in the event of a service interruption, whether natural or man-made. For example, in the event of a disaster scenario at one location, machines at different locations may protect applications in that location. This Security as a Service offering is a reactive, protective, and detective technical control.
14.4.10 Network Security
Network Security consists of security services that restrict or allocate access and that distribute, monitor, log, and protect the underlying resource services.
Architecturally, network security provides services that address security controls at the network in aggregate or those controls specifically addressed at the individual network of each underlying resource. In cloud / virtual environments and hybrid environments, network security is likely to be provided by virtual devices alongside traditional physical devices. Tight integration with the hypervisor to ensure full visibility of all traffic on the virtual network layer is key. These Network Security offerings include detective, protective, and reactive technical controls.
14.5 Permissions
A) Implementers may employ pattern recognition of user activities..
B) Implementers may employ secure legal mediation of security metrics for SLA expectation management
C) Implementers may employ provide trusted channels for penetration testing.
14.6 Recommendations
a) Implementers should ensure secure communication channels between tenant and consumer.
b) Providers should supply automated secure and continuous notification throughout the supply chain on a need-to-know basis.
c) Providers should supply secured logging of internal operations for service level agreement compliance.
d) Consumers should request addition of third party audit and SLA mediation services.
e) All parties should enable Continuous Monitoring of all interfaces through standardized security interfaces such as SCAP (NIST), CYBEX (ITU-T), or RID & IODEF (IETF).
14.7 Requirements
14.7.1 Identity as a Service Requirements
1) Providers of IaaS must provide cloud customers provisioning/de-provisioning of accounts (of both cloud & on-premise applications and resources).
2) Providers of IaaS must provide cloud customers authentication (multiple forms and factors).
3) Providers of IaaS must provide cloud customers identity life cycle management.
4) Providers of IaaS must provide cloud customers directory services.
5) Providers of IaaS must provide cloud customers directory synchronization (multi-lateral as required).
6) Providers of IaaS must provide cloud customers federated SSO.
7) Providers of IaaS must provide cloud customers web SSO (granular access enforcement & session management - different from federated SSO).
8) Providers of IaaS must provide privileged session monitoring.
9) Providers of IaaS must provide granular access management.
10) Providers of IaaS must provide tamper-proof storage of audit records (including an option for non-repudiation).
11) Providers of IaaS must provide policy management (incl. authorization management, role management, compliance policy management).
12) Providers of IaaS must provide cloud customers authorization (both user and application/system).
13) Providers of IaaS must provide cloud customers authorization token management and provisioning.
14) Providers of IaaS must provide cloud customers user profile and entitlement management (both user and application/system).
15) Providers of IaaS must provide cloud customers support for policy and regulatory compliance monitoring and/or reporting.
16) Providers of IaaS must provide cloud customers federated provisioning of cloud applications.
17) Providers of IaaS must provide privileged user and password management (including administrative, shared, system and application accounts).
18) Providers of IaaS must provide cloud customers Role-Based Access Control (RBAC) (where supported by the underlying system/service).
19) Providers of IaaS must provide cloud customers optionally support DLP integration.
20) Providers of IaaS must provide cloud customers optionally support granular activity auditing broken down by individual.
21) Providers of IaaS must provide cloud customers segregation of duties based on identity entitlement.
22) Providers of IaaS must provide cloud customers compliance-centric reporting.
23) Providers of IaaS must provide cloud customers centralized policy management.
25) Providers of IaaS must provide cloud customers usable management interfaces.
26) Providers of IaaS must provide cloud customers unified access control & audit.
27) Providers of IaaS must provide cloud customers Interoperability and heterogeneity among various providers.
28) Providers of IaaS must provide cloud customers scalability.
14.7.2 DLP SecaaS Requirements
1) Providers of DLP must provide cloud customers with data labeling and classification.
2) Providers of DLP must provide cloud customers with identification of Sensitive Data.
3) Providers of DLP must provide cloud customers with predefined policies for major regulatory statues.
4) Providers of DLP must provide cloud customers with context detection heuristics.
5) Providers of DLP must provide cloud customers with structured data matching (data-at-rest).
6) Providers of DLP must provide cloud customers with SQL regular expression detection.
7) Providers of DLP must provide cloud customers with traffic spanning (data-in-motion) detection.
8) Providers of DLP must provide cloud customers with Real Time User Awareness.
9) Providers of DLP must provide cloud customers with security level assignment.
10) Providers of DLP must provide cloud customers with custom attribute lookup.
11) Providers of DLP must provide cloud customers with automated incident response.
12) Providers of DLP must provide cloud customers with signing of data.
13) Providers of DLP must provide cloud customers with cryptographic data protection and access control.
14) Providers of DLP must provide cloud customers with machine-readable policy language.
14.7.3 Web Services SecaaS Requirements
1) Providers of Web Services SecaaS must provide cloud customers with web monitoring and filtering.
2) Providers of Web Services SecaaS must provide cloud customers with Malware, Spyware, and Bot Network analyzer and blocking.
3) Providers of Web Services SecaaS must provide cloud customers with phishing site blocker.
4) Providers of Web Services SecaaS must provide cloud customers with instant messaging scanning.
5) Providers of Web Services SecaaS must provide cloud customers with email security.
6) Providers of Web Services SecaaS must provide cloud customers with bandwidth management / traffic control.
7) Providers of Web Services SecaaS must provide cloud customers with Data Loss Prevention.
8) Providers of Web Services SecaaS must provide cloud customers with fraud prevention.
9) Providers of Web Services SecaaS must provide cloud customers with Web Access Control.
10) Providers of Web Services SecaaS must provide cloud customers with backup.
11) Providers of Web Services SecaaS must provide cloud customers with SSL (decryption / hand off).
12) Providers of Web Services SecaaS must provide cloud customers with usage policy enforcement.
13) Providers of Web Services SecaaS must provide cloud customers with vulnerability management.
14) Providers of Web Services SecaaS must provide must provide cloud customers with web intelligence reporting.
14.7.4 Email SecaaS Requirements
1) Providers of Email Security SecaaS must provide cloud customers with accurate filtering to block spam and phishing.
2) Providers of Email Security SecaaS must provide cloud customers with deep protection against viruses and spyware before they enter the enterprise perimeter.
3) Providers of Email Security SecaaS must provide cloud customers with flexible policies to define granular mail flow and encryption.
4) Providers of Email Security SecaaS must provide cloud customers with rich, interactive reports and correlate real-time reporting.
5) Providers of Email Security SecaaS must provide cloud customers with deep content scanning to enforce policies.
6) Providers of Email Security SecaaS must provide cloud customers with the option to encrypt some / all emails based on policy.
7) Providers of Email Security SecaaS must provide cloud customers with integration capability to various email server solutions.
14.7.5 Security Assessment SecaaS Requirements
1) Providers of Security Assessment SecaaS must provide cloud customers with detailed governance processes and metrics (Implementers should define and document and process by which policies are set and decision making is executed).
2) Providers of Security Assessments and Governance offerings should implement an automated solution for notifying members of their immediate supply chain in the event of breach or security incident.
3) Providers of Security Assessment SecaaS must provide cloud customers with proper risk management (Implementers should define and document and process for ensuring that important business processes and behaviors remain within the tolerances associated with those policies and decisions).
4) Providers of Security Assessment SecaaS must provide cloud customers with details of compliance (Implementers should define and document process-of-adherence to policies and decisions).
5) Providers of Security Assessment SecaaS must provide cloud customers with policies that can be derived from internal directives, procedures, and requirements or external laws, regulations, standards and agreements.
6) Providers of Security Assessment SecaaS must provide cloud customers with technical compliance audits (automated auditing of configuration settings in devices, operating systems, databases, and applications).
7) Providers of Security Assessment SecaaS must provide cloud customers with application security assessments (automated auditing of custom applications).
8) Providers of an assessment and governance service offering must provide cloud customers with vulnerability assessments—automated probing of network devices, computers, and applications for known vulnerabilities and configuration issues.
9) Providers of Security Assessment SecaaS must provide cloud customers with penetration testing (exploitation of vulnerabilities and configuration issues to gain access to an environment, network or computer, typically requiring manual assistance)
10) Providers of Security Assessment SecaaS must provide cloud customers with a security rating.
14.7.6 Intrusion Detection SecaaS Requirements
1) Providers of Intrusion Detection SecaaS must provide cloud customers with identification of intrusions and policy violations.
2) Providers of Intrusion Detection SecaaS must provide cloud customers with automatic or manual remediation actions.
3) Providers of Intrusion Detection SecaaS must provide cloud customers with Coverage for Workloads, Virtualization Layer (VMM/Hypervisor) Management Plane
4) Providers of Intrusion Detection SecaaS must provide cloud customers with deep packet inspection using one or more of the following techniques: statistical, behavioral, signature, heuristic.
5) Providers of Intrusion Detection SecaaS must provide cloud customers with system call monitoring.
6) Providers of Intrusion Detection SecaaS must provide cloud customers with system/application log inspection.
7) Providers of Intrusion Detection SecaaS must provide cloud customers with integrity monitoring OS (files, registry, ports, processes, installed software, etc.)
8) Providers of Intrusion Detection SecaaS must provide cloud customers with integrity monitoring VMM/Hypervisor.
9) Providers of Intrusion Detection SecaaS must provide cloud customers with VM Image Repository Monitoring.
14.7.7 SIEM SecaaS Requirements
1) Providers of SIEM SecaaS must provide cloud customers with real time log /event collection, de-duplication, normalization, aggregation and visualization.
2) Providers of SIEM SecaaS must provide cloud customers with forensics support.
3) Providers of SIEM SecaaS must provide cloud customers with reporting and support.
4) Providers of SIEM SecaaS must provide cloud customers with IR support.
5) Providers of SIEM SecaaS must provide cloud customers with anomaly detection not limited to email.
6) Providers of SIEM SecaaS must provide cloud customers with detailed reporting.
7) Providers of SIEM SecaaS must provide cloud customers with flexible data retention periods and flexible policy management
14.7.8 Encryption SecaaS Requirements
1) Providers of Encryption SecaaS must provide cloud customers with protection of data in transit.
2) Providers of Encryption SecaaS must provide cloud customers with protection of data at rest.
3) Providers of Encryption SecaaS must provide cloud customers with key and policy management.
4) Providers of Encryption SecaaS must provide cloud customers with protection of cached data.
14.7.9 Business Continuity and Disaster Recovery Requirements
1) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with flexible infrastructure.
2) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with secure backup.
3) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with monitored operations.
4) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with third party service connectivity.
5) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with replicated infrastructure component.
6) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with replicated data (core / critical systems).
7) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with data and/or application recovery.
8) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with alternate sites of operation.
9) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with tested and measured processes and operations to ensure operational resiliency.
10) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with geographically distributed data centers / infrastructure.
11) Providers of Business Continuity & Disaster Recovery SecaaS must provide cloud customers with Network survivability.
14.7.10 Network Security SecaaS Requirements
1) Providers of Network Security SecaaS must provide cloud customers with details of data threats.
2) Providers of Network Security SecaaS must provide cloud customers with details of access control threats.
3) Providers of Network Security SecaaS must provide cloud customers with access and authentication controls.
4) Providers of Network Security SecaaS must provide cloud customers with security gateways (firewalls, WAF, SOA/API).
5) Providers of Network Security SecaaS must provide cloud customers with security products (IDS/IPS, Server Tier Firewall, File Integrity Monitoring, DLP, Anti-Virus, Anti-Spam).
6) Providers of Network Security SecaaS must provide cloud customers with security monitoring and incident response.
7) Providers of Network Security SecaaS must provide cloud customers with DoS protection/mitigation.
8) Providers of Network Security SecaaS must provide cloud customers with Secure “base services” like DNSSEC, NTP, OAuth, SNMP, management network segmentation, and security.
9) Providers of Network Security SecaaS must provide cloud customers with traffic / netflow monitoring.
10) Providers of Network Security SecaaS must provide cloud customers integration with Hypervisor layer.
===// END //===